It came to light recently that a vulnerability exists in a script used widely by WordPress Theme authors, including those by Elegant Themes, which I highly recommend.
This is an easy bug to fix, but that requires users to update their WordPress themes (not just the core installation), and we know that site maintenance is an easy thing to postpone in a busy world.
 What’s the risk?
What’s the risk?
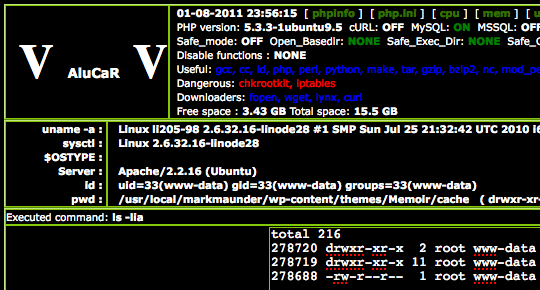
If attack.php is a hacker shell app like Alucar shell, you have access to the server with whatever priveleges the web server account has. e.g. you can read /etc/passwd
That is to say, the hacker could do anything – replace your site, mine your data, lock you out, anything. No doubt you’ve come across hijacked sites reduced to skulls and flames proclaiming ‘Hacked!’ in Russian or Brazilian?
The user reporting the vulnerability said:
My server was compromised earlier today. I tracked it down to timthumb.php and confirmed the attack script was in the timthumb cache directory.
A file containing a base64 encoded Alucar shell was uploaded, executed and the attacker used the shell to inject ads into my blog. He/she may have done a lot more damage that I’m not aware of yet.
What to do?
Verify your automated backup system, and keep your WordPress installation, your plugins and your themes updated!
Thanks to Nick at ET for the swift notice. Read the original report.